Restore Buffer Overflow Attacks: Breaking Undo-Based Defense Schemes
Abstract
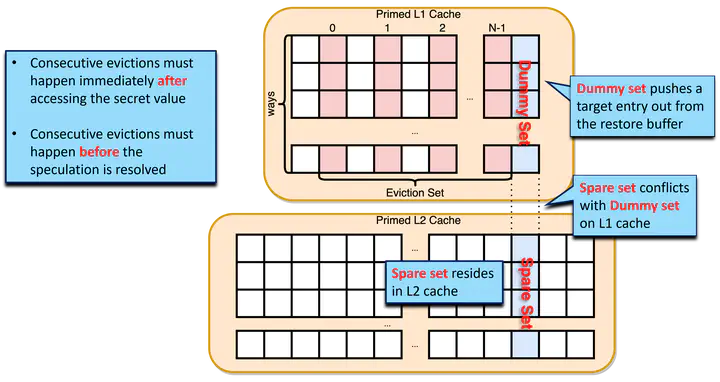
Transient execution attacks have been severe security threats since such attacks exploit architectural vulnerabilities in out-of-order processors. Researchers proposed several architectural solutions to defend against transient execution attacks. By restoring the victim blocks stored temporarily in a restore buffer, the undo-based approaches can revoke the cache state changed by speculative loads. Thus it is known that the undo-based defense mechanisms can protect processors from transient execution attacks.In this paper, we reveal the undo-based protection scheme is still vulnerable to the elaborated Prime+Probe type attacks. Under the undo-based protection, the victim blocks by the speculative loads are stored in the restore buffer that has limited resources. Thus if the restore buffer is full, part of the victim blocks in the restore buffer can be evicted from the restore buffer. Then the cache state cannot be restored since the processor cannot find the victim blocks required for restoring the cache state. We design a restore buffer overflow attack that can leak secret data even if the processor is protected under the undo-based scheme. We evaluate the attack mechanism using the architectural simulator. Our evaluation exhibits that the attack can leak part of secret data successfully.