Vizard: Passing over Profiling-Based Detection by Manipulating Performance Counters
Abstract
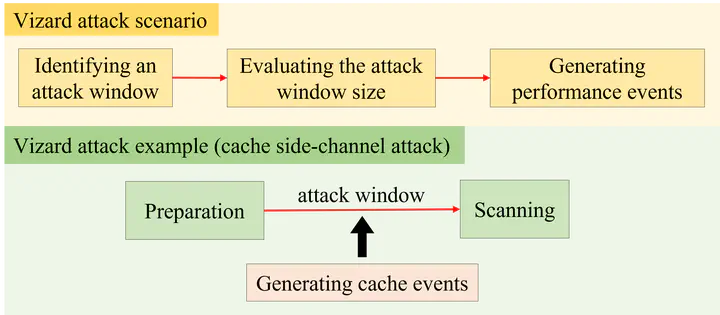
Cache side-channel attacks have been serious security threats to server computer systems, thus researchers have proposed software-based defense approaches that can detect the security attacks. Profiling-based detectors are lightweight detection solutions that rely on hardware performance counters to identify unique cache performance behaviors by cache side-channel attacks. The detectors typically need to set appropriate criteria to differentiate between attack processes and normal applications. In this paper, we explore the limitations of profiling-based detectors that rely on hardware performance counters. We present an attack scenario, called Vizard, that can bypass the existing profiling-based detectors by manipulating cache performance behaviors of an attack process. Our analysis discloses that cache side-channel attacks include idle periods that can be exploited as attack windows for creating cache events. Vizard generates counterbalancing cache events within the attack windows to hide particular cache performance behaviors of cache side-channel attacks. Our evaluation exhibits that Vizard can effectively bypass profiling-based detectors while maintaining high attack success rates. Our research work represents that attackers can bypass the existing detection approaches by manipulating performance counters.